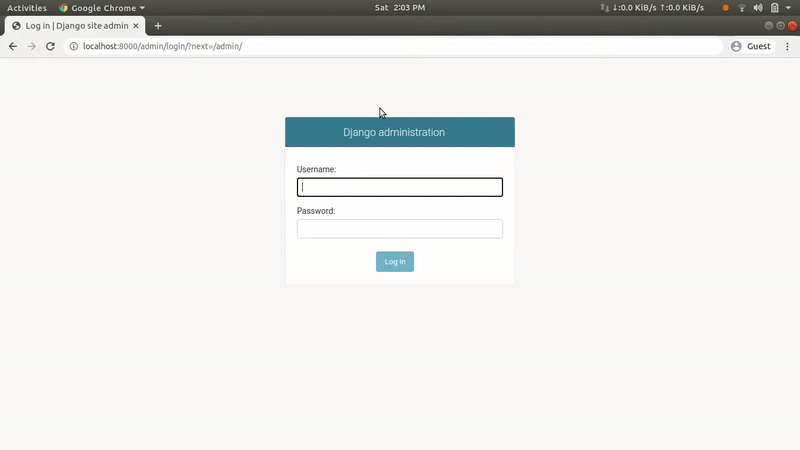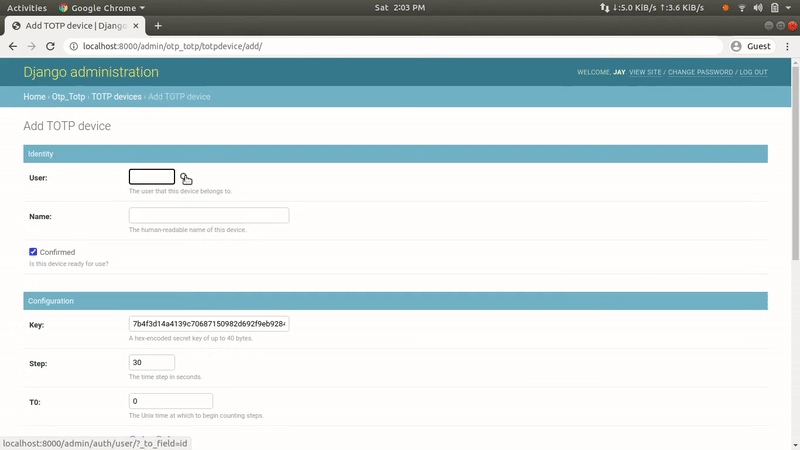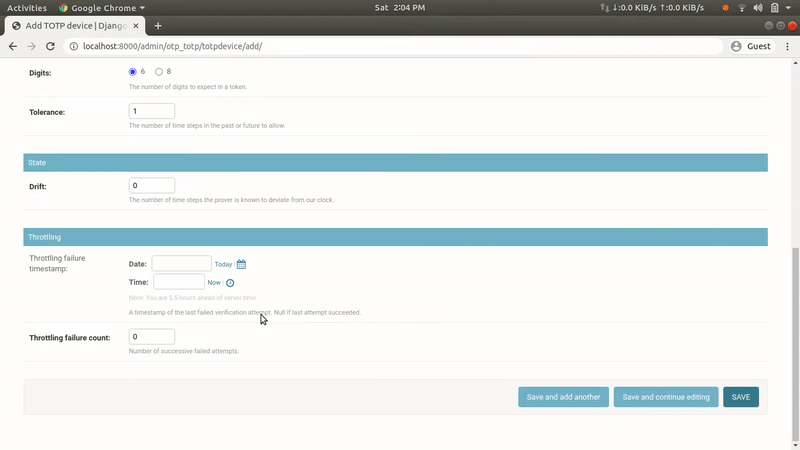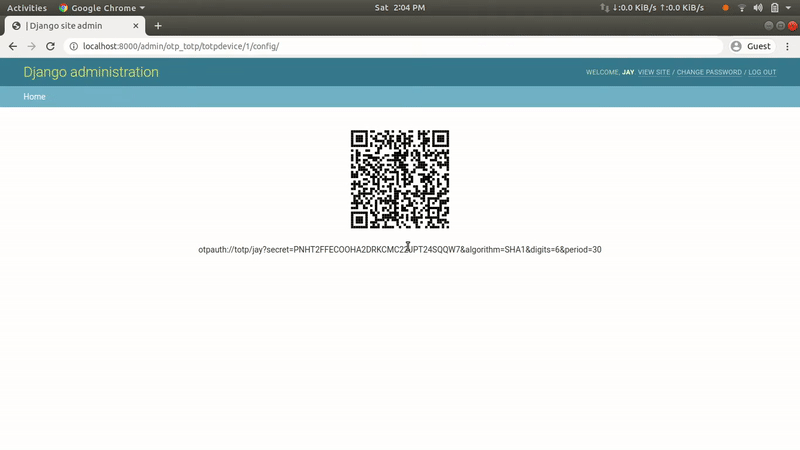
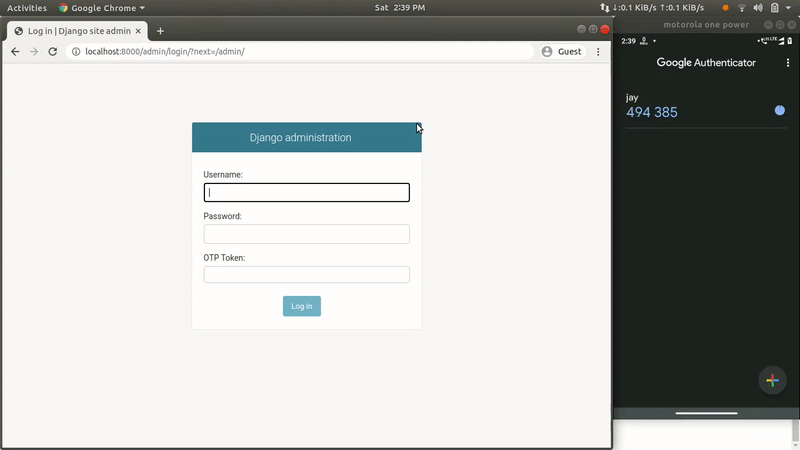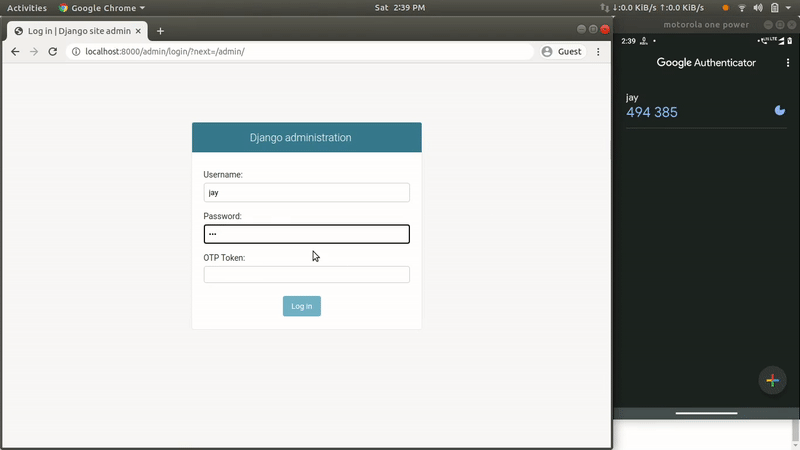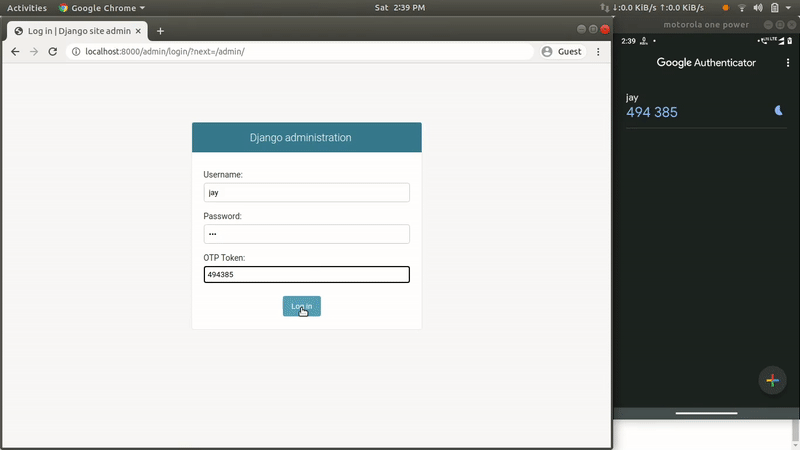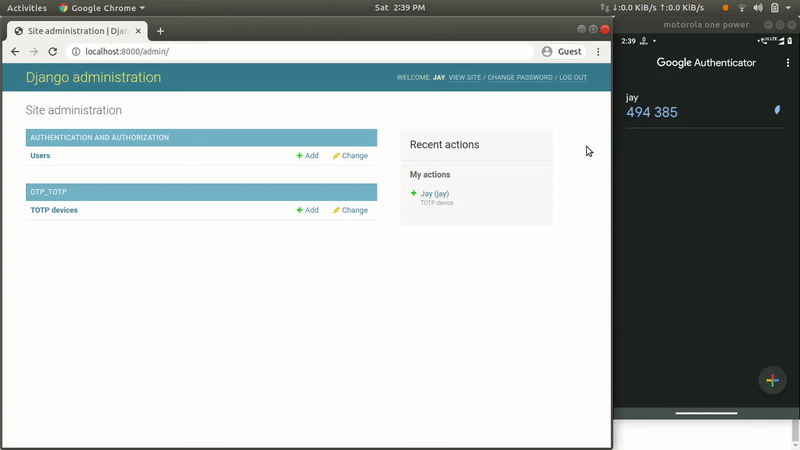
Add 2FA (Two Factor Authentication) using a token generator app like Google Authenticator.
A safe is merely safe till there is a reliable lock protecting it! In this article, I’m going to talk about strengthening the login mechanism of the Django Admin Panel by adding another layer of security.
Two-factor authentication (2FA in short) is one of the many methods of Multi-factor authentication that adds an extra layer of security along with login credentials to confirm user identity. In 2FA, users confirm their identities by a combination of two different factors: 1) something they know, 2) something they have, or 3) something they are.
Here I’m going to build a mechanism where admin users will be prompted to add a Time-based One-time Password (TOTP) at the time of login. As the name “TOTP” suggests, the generated token will only be valid for a specific amount of time (i.e. 30 seconds), and after that, a new token will be auto-generated.